Software supply chains are under attack like never before. High-profile breaches, like SolarWinds and Codecov, have shown how vulnerabilities in one component can compromise entire ecosystems. If your business relies on software, securing its supply chain isn’t optional – it’s a must to protect your data, reputation, and operations.
Here’s what you need to know:
- What’s at risk? Every element in your software supply chain, from third-party libraries to CI/CD pipelines, can be exploited by attackers.
- Common attack methods: Dependency hijacking, tampered updates, and compromised developer tools are just a few ways attackers infiltrate systems.
- Why it matters: Without a strategy, your business is exposed to malicious code, data theft, and operational disruptions.
- Solutions to secure your supply chain:
- Use frameworks like NIST’s Secure Software Development Framework (SSDF).
- Implement Software Bills of Materials (SBOMs) to track and verify components.
- Strengthen vendor management and enforce secure development practices.
The stakes are high, but by taking action now, you can reduce risks and build trust with your customers.
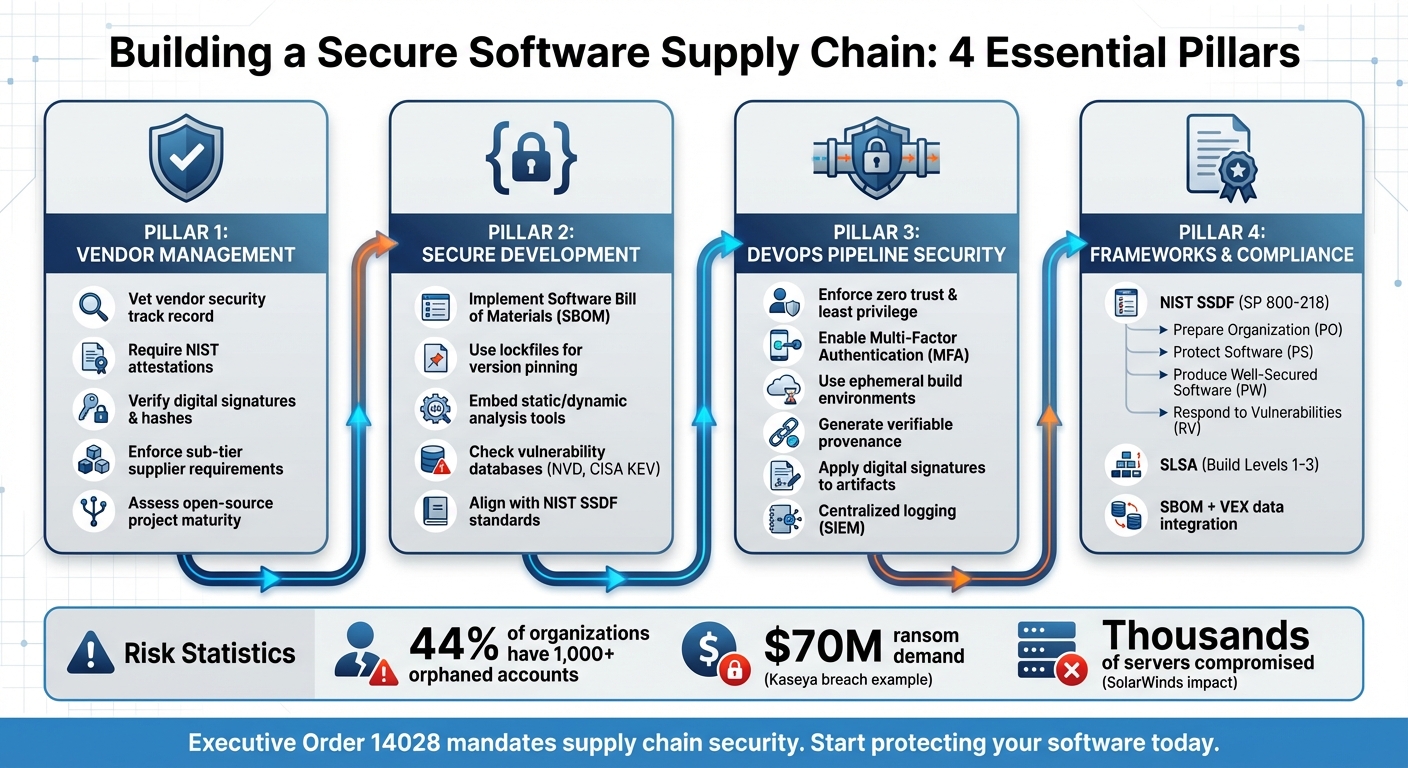
4-Step Framework for Software Supply Chain Security Implementation
How Supply Chain Attacks Work
Common Attack Methods
Modern software development relies on a web of dependencies, and attackers know how to exploit this complexity. One common method is dependency hijacking, where fake versions of legitimate software libraries are created or existing third-party packages are compromised to inject malicious code. A striking example is Alex Birsan’s demonstration, where he breached major companies by using fake dependencies.
Another tactic involves manipulating software updates. Attackers can inject malicious code or backdoors into legitimate updates, compromising every user who installs them. Similarly, vulnerabilities in CI/CD pipelines allow attackers to embed harmful code during development. By stealing code-signing certificates, attackers make malicious software appear as trusted updates from legitimate vendors.
Even development environments are not immune. Weaknesses in tools like integrated development environments, code editors, and plugins can open doors for attackers. Exploits targeting version control systems, such as Git, can also enable them to inject malicious code or take over privileged accounts used in building software.
These methods highlight how attackers exploit technical systems, but the risks don’t stop there. External partnerships introduce further vulnerabilities.
Risks from Vendors and Third Parties
Third-party vendors often represent a weak link in an organization’s defenses. Attackers target these relationships to bypass traditional security measures. When software is sourced from external suppliers, organizations lose visibility into how it’s developed, integrated, and deployed.
"Instead of directly targeting enterprises, they are infiltrating trusted third-party vendors, leveraging supply chain weaknesses to gain stealthy and long-term access to critical enterprise systems." – Anil Agrawal, Security Researcher, Vorlon
Managed Service Providers (MSPs) are especially tempting targets. Attacking one MSP can give hackers access to multiple downstream clients at once. For example, in early 2025, the APT group Silk Typhoon exploited a zero-day vulnerability in Ivanti Pulse Connect VPN (CVE-2025-0282). This allowed them to access high-value targets, reset admin accounts, and deploy web shells.
Attackers also exploit non-human identities, such as service principals, OAuth apps, and API keys, to move laterally across interconnected SaaS applications and cloud environments. With 44% of organizations reporting over 1,000 orphaned accounts, these overlooked vulnerabilities pose a serious threat.
Case Studies of Supply Chain Breaches
Real-world examples bring these risks into sharp focus. In December 2020, the SolarWinds attack inserted a backdoor into a software update for the Orion networking tool. This gave attackers remote access to thousands of corporate and government servers, showing how a single compromised update can ripple across an entire ecosystem.
The 2021 Kaseya breach demonstrated a similar impact. A malicious update infected thousands of environments, leading to a $70 million ransom demand.
In April 2021, the Codecov attack revealed how even small tools can be dangerous. Attackers modified the Bash uploader script used in CI/CD pipelines to steal customer credentials and data. More recently, in February 2026, a compromised developer account was used to spread "GlassWorm" malware through the Open VSX Registry, targeting popular developer tools and extensions.
These cases reveal a troubling pattern: attackers exploit trust and target the weakest links in the supply chain. Whether through tampered updates, compromised MSPs, or vulnerable development tools, the damage can spread far and wide.
Software Supply Chain Explained: Risks, Stages, and How to Secure It
Frameworks and Tools for Supply Chain Security
To protect software supply chains, organizations rely on structured frameworks and tools. These frameworks provide essential guidance for securing every phase of software development, ensuring a proactive approach to potential threats.
NIST Secure Software Development Framework (SSDF)
The NIST Secure Software Development Framework (NIST SP 800-218) offers a structured approach to secure software development. It provides a shared vocabulary for software producers and buyers, enabling clear communication about secure practices throughout the software lifecycle, not just for individual releases.
This framework is divided into four key areas:
- Prepare the Organization (PO): Focuses on policies, procedures, and team readiness.
- Protect the Software (PS): Aims to safeguard software components against tampering.
- Produce Well-Secured Software (PW): Ensures secure development practices to minimize vulnerabilities.
- Respond to Vulnerabilities (RV): Addresses post-release vulnerability identification and remediation.
These categories integrate seamlessly into existing Software Development Life Cycle (SDLC) models, reducing vulnerabilities and mitigating risks when exploits occur. Organizations can verify security practices through attestation, which demonstrates adherence to secure development standards. For higher-risk scenarios, second- or third-party attestations are recommended over self-attestation.
| SSDF Category | Key Focus Areas | Relevant C-SCRM Controls |
|---|---|---|
| Prepare the Organization (PO) | Policy, procedures, and people preparation | SA-1 (Policy), SA-3 (SDLC), SR-3 (Supply Chain Controls) |
| Protect the Software (PS) | Protecting all components of the software from tampering | SA-8 (Engineering Principles), SR-4 (Provenance) |
| Produce Well-Secured Software (PW) | Producing secure software with minimal vulnerabilities | SA-11 (Developer Testing), SA-15 (Development Process) |
| Respond to Vulnerabilities (RV) | Identifying and remediating vulnerabilities post-release | SA-5 (Documentation), SA-10 (Configuration Management) |
Supply-chain Levels for Software Artifacts (SLSA)

SLSA (pronounced "salsa") provides a standardized framework to ensure build integrity and tamper resistance. It is structured into tracks and levels, with the Build Track being the most advanced. The framework outlines three levels of security assurance:
- Build L1 (Provenance): Requires an attestation describing how the package was built. While straightforward, it is relatively easy to forge.
- Build L2 (Build Service): Builds must occur on a hosted service that generates and signs provenance, adding tamper resistance.
- Build L3 (Hardened Builds): Requires a hardened build service with strict isolation to prevent interference between builds.
"Having a common language and standard for objectively measuring our supply chain security is a must in order to even begin meeting EO 14028." – Trishank Karthik Kuppusamy, Staff Security Engineer, Datadog
Implementing SLSA involves three steps: defining project-specific security expectations, automatically generating provenance during builds, and verifying provenance before publication or use. The cornerstone of this process is provenance, which documents how, when, and by whom an artifact was built. However, security only becomes effective when this provenance is verified against predefined standards.
Software Bill of Materials (SBOM)
An SBOM acts as a detailed inventory of all software components, including their origins and relationships. This transparency is critical for identifying vulnerabilities in open-source or third-party components. The push for SBOM adoption gained momentum with Executive Order 14028, which emphasized strengthening the nation’s cybersecurity.
"A ‘software bill of materials’ (SBOM) has emerged as a key building block in software security and software supply chain risk management." – CISA
SBOMs empower organizations to quickly assess their exposure to newly discovered vulnerabilities, offering critical insight into the origins and histories of software components. They also serve as a measure of a developer’s or supplier’s commitment to secure practices.
Pairing SBOMs with Vulnerability Exploitability eXchange (VEX) data enhances risk assessments by confirming whether vulnerabilities in components are actually exploitable. This allows teams to focus on genuine threats rather than potential risks. In high-stakes scenarios, such as national security or mission-critical functions, organizations should demand more detailed SBOMs, including vendor-level vulnerability disclosures.
sbb-itb-05efa2a
How to Reduce Supply Chain Security Risks
Taking practical steps to secure your software supply chain is essential at every stage, from vendor selection to deployment. Here’s how to safeguard your organization against potential threats.
Vendor Management and Acquisition Practices
The first step in protecting your supply chain is thoroughly vetting your vendors. Assess their security track record, the maturity of their components, and how they’ve handled vulnerabilities in the past. For open-source projects, check if the project is actively maintained, has a strong contributor base, updates its dependencies regularly, and has a clear process for reporting and fixing vulnerabilities.
"Organizations are concerned about the risks associated with products and services that may potentially contain malicious functionality, are counterfeit, or are vulnerable due to poor manufacturing and development practices within the supply chain." – NIST SP 800-161 Rev. 1
To strengthen security, require vendors to provide attestations that align with NIST guidelines. In high-risk cases, prioritize third-party attestations over self-attestations. Extend these security requirements to sub-tier suppliers through contracts that enforce secure development, delivery, and maintenance practices. Additionally, always verify hashes and digital signatures for vendor-supplied software installations and updates to ensure their integrity.
| Capability Level | Recommended Vendor Risk Assessment Practices |
|---|---|
| Foundational | Use open-source data and security ratings to assess vendors; require self-attestation to NIST SP 800-218; verify hashes/signatures for updates. |
| Sustaining | Require third-party attestation to SSDF V1.1; enforce flow-down requirements for sub-tier suppliers; prioritize vendors offering software security labels. |
| Enhancing | Demand periodic third-party attestations for advanced SSDLC capabilities (e.g., automated rollbacks, staggered deployments); use just-in-time credentials for build systems. |
Once vendor management is in place, focus on secure development practices to minimize risks further.
Secure Development and Dependency Management
Using tools like lockfiles (e.g., package-lock.json) for version pinning and maintaining a Software Bill of Materials (SBOM) can help you track both direct and transitive dependencies. Regularly check vulnerability databases, such as the National Vulnerability Database and the CISA Known Exploited Vulnerabilities catalog, to identify risks in third-party components.
Build security into your Software Development Life Cycle (SDLC) by embedding static and dynamic analysis tools directly into your processes. These tools can automatically scan libraries and packages for vulnerabilities, especially when open-source components are involved. Set restrictions on open-source usage and use automated verification to flag unsupported or potentially harmful subcomponents. Align these practices with SSDF standards to ensure comprehensive protection.
"Federal agencies… should, at a minimum, implement the same security controls internally that they require of their software suppliers." – NIST
Pair these strategies with secure DevOps practices to protect your entire build pipeline.
Building Secure DevOps Pipelines
A secure DevOps pipeline starts with enforcing zero trust principles, including least privilege access and clear separation of duties within build and version control systems. Multi-Factor Authentication (MFA) is a must, and credentials should be rotated regularly to prevent account takeovers. This is especially important given that 44% of organizations report having 1,000 or more orphaned accounts, which pose hidden risks.
Use ephemeral build environments that are destroyed after each use to avoid cache poisoning or persistent malicious injections. During the build process, generate verifiable provenance to document when, where, and how artifacts were created. Digital signatures should be applied to all components and validated before deployment.
Keep your CI/CD configurations and build scripts under version control for peer review and auditability. Minimize user-controllable parameters in the build process to reduce the chance of tampering, and implement centralized logging (SIEM) to monitor version control, build, and delivery systems for unauthorized access or configuration changes.
"A flaw in a single component, such as a vulnerable third-party dependency or misconfigured VCS, can put an entire SSC [Software Supply Chain] in jeopardy." – OWASP
How Equifier Can Help Build Your Security Strategy
Equifier strengthens supply chain security by pinpointing vulnerabilities, ensuring compliance, and embedding security measures into every phase of development.
Risk Assessments and Compliance Solutions
Equifier employs a risk assessment framework that aligns with NIST SP 800-161 Rev. 1, examining cybersecurity risks across all organizational levels. This process evaluates development and deployment practices to uncover supplier vulnerabilities. By using the SCRM Assessment Scoping Questionnaire outlined in NIST Table 26, Equifier determines the scope of supply chain evaluations, identifying risks such as malicious functionality, counterfeit products, and weaknesses caused by inadequate development practices.
"Organizations are concerned about the risks associated with products and services that may potentially contain malicious functionality, are counterfeit, or are vulnerable due to poor manufacturing and development practices within the supply chain." – NIST SP 800-161 Rev. 1
The assessment incorporates Software Bill of Materials (SBOM) analysis to uncover vulnerabilities in third-party components and open-source dependencies. Equifier also ensures that software producers adhere to the Secure Software Development Framework (SSDF) and provide attestations verifying compliance with secure practices. This systematic approach enables businesses to demand greater transparency from vendors and apply consistent evaluation criteria across suppliers.
These insights naturally feed into Equifier’s continuous monitoring and support services.
Managed Security Services
After identifying risks, Equifier’s managed security services offer ongoing monitoring of deployed software to detect vulnerabilities from updates or new threats. These services leverage automated tools, such as DAST, to identify and address threats in real time. They also automatically flag security, quality, and license compliance risks in open-source and third-party dependencies, reducing the workload for internal teams.
Custom IT Consulting for Secure SDLC
Equifier complements its automated solutions with expert consulting to integrate security practices into your development lifecycle. Their consultants help businesses align their SDLC with NIST standards through measures like threat modeling, automated verification, and component tracking. They also assist in setting up secure build environments, which include automated deployments, staggered production releases, and just-in-time credentials for build systems.
"SBOMs hold the potential to provide increased transparency, provenance, and speed at which vulnerabilities can be identified and remediated." – NIST
Equifier helps enforce security requirements across all supplier levels, ensuring supply chain integrity from end to end. By adopting a tiered maturity model – Foundational, Sustaining, and Enhancing – organizations can focus on security capabilities that align with their risk profile and operational needs.
Conclusion: Building a Secure Software Supply Chain
Protecting your software supply chain is no longer optional – it’s a critical step in safeguarding your business against increasingly advanced cyber threats. The risks are very real, ranging from malicious code and counterfeit components to vulnerabilities caused by poor development practices. Addressing these challenges requires deliberate, proactive measures.
A strong starting point is adopting Software Bills of Materials (SBOMs), which provide transparency into every component of your software stack. Pair this with aligning your processes and vendor requirements to the NIST Secure Software Development Framework (SSDF). Additionally, NIST SP 800-161r1’s "Foundational, Sustaining, and Enhancing" approach offers a way to tailor your security measures based on your specific risk profile. These tools don’t just help with compliance – they build a robust defense for your software assets.
The importance of this issue was highlighted by Executive Order 14028, which positioned software supply chain security as a key focus of national cybersecurity efforts. Federal agencies, led by NIST, continue to refine their guidance on C-SCRM and SBOMs, signaling the need for organizations to act swiftly.
Delaying action only increases your exposure to risks. By adopting a proactive security strategy now, you position your organization to respond faster to incidents, meet regulatory requirements, and save on costs tied to reactive fixes and breaches. The real question isn’t whether to secure your software supply chain – it’s how quickly you can implement these critical safeguards.
FAQs
What is an SBOM, and why does it matter for software security?
A Software Bill of Materials (SBOM) is essentially the ingredient list for a software product. It outlines all the components that make up the software, including open-source libraries and third-party tools. This level of transparency is crucial for spotting and addressing vulnerabilities in the software supply chain.
With an SBOM, organizations can more effectively evaluate security risks, meet industry compliance requirements, and respond swiftly to threats like the Log4j or SolarWinds incidents. Keeping an SBOM up to date allows companies to bolster their software’s security and minimize the dangers posed by compromised or outdated components.
What is dependency hijacking in software supply chains and how does it work?
Dependency hijacking occurs when attackers compromise upstream components in the software supply chain – like third-party libraries or package repositories – by injecting malicious code. This tampered code can then spread unknowingly to downstream users, creating the potential for widespread security vulnerabilities.
These attacks take advantage of the trust developers place in widely used dependencies. That’s why it’s so important to carefully vet and monitor every component in your software supply chain. Steps like verifying the source of dependencies, relying on secure repositories, and keeping dependencies up to date can go a long way in reducing this risk.
What are the main components of the NIST Secure Software Development Framework (SSDF)?
The NIST Secure Software Development Framework (SSDF) provides a structured approach to building safer software by embedding security measures directly into the development process. Its primary aim is to identify weaknesses early, ensure secure design and coding practices, and manage risks throughout the software’s lifecycle.
Key principles of the framework include secure coding practices, routine testing and validation, and proactive monitoring for new threats. By following these guidelines, organizations can align their processes with industry standards, minimizing vulnerabilities and strengthening the reliability of their software.









